14) which of the following are breach prevention best practices
There are steps and practices that you can implement for breach prevention. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary andby promptly.
Crowdstrike Falcon Elite Advanced Breach Prevention
Create Strong Policies Strong Passwords.
. 14 which of the following are breach prevention best practices. Administrative actions and policies and procedures that are used to manage the selection development implementation and maintenance of security measures to protect electronic PHI. Which Of The Following Are Breach Prevention Best Practices.
Implementing encryption standards and backup policies to decrease risks and make sure that. A breach as defined by the dod is broader than a hipaa breach or breach defined by hhs. Vulnerability assessment is the process intended to identify classify and prioritize security threats and.
Which of the following are breach prevention best practices. 30 Best Practices for Preventing a Data Breach. Access only the minimum.
Best practices for breach prevent are. Which of the following are breach prevention best practices. Public Health Nigeria Public Health Nigeria an Interdisciplinary public health movement focused on health education advancing fair public health policies promoting.
Which of the following are breach prevention best practices. A- Access only the minimum amount of PHIpersonally identifiable information PII necessary. Which of the following are breach prevention best practices.
The following are high-level best practices for preventing breaches. Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022. Identify areas that store transmit collect or process.
Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. The worst part is that the sensitive data even if its not stolen copied or deleted when the wrong unauthorized. Identity sensitive data collected stored transmitted or processes.
Companies that leveraged artificial intelligence machine learning. It is better to acknowledge that data breaches are inevitable than to assume your organization is. Promptly retrieve documents containing PHIPHI from the printer.
Managers Have A Role In Supporting Staff To Follow Data Breach Prevention Practices As Well As Acting Quickly In The Event Of A Data Breach. Developing policies and procedures. Making weak passwords can be a reason for Data.
Invest in security automation. Perform suspicious email training exercises to help employees identify potentially nefarious emails. Logoff or lock your workstation when it is unattended.
Developing the IRP will help the IT staff of the company to control the data breach incidents.

Principle Of Least Privilege Cycode

Audit Log Review And Management Best Practices Strongdm
Board Oversight Of Cyber Risks And Cybersecurity

The Top 20 Security Predictions For 2020

6 Most Common Causes Of Data Leaks In 2022 Upguard

The Future Of Data Loss Prevention Mckinsey Company

Cyber Resilience Security Insider
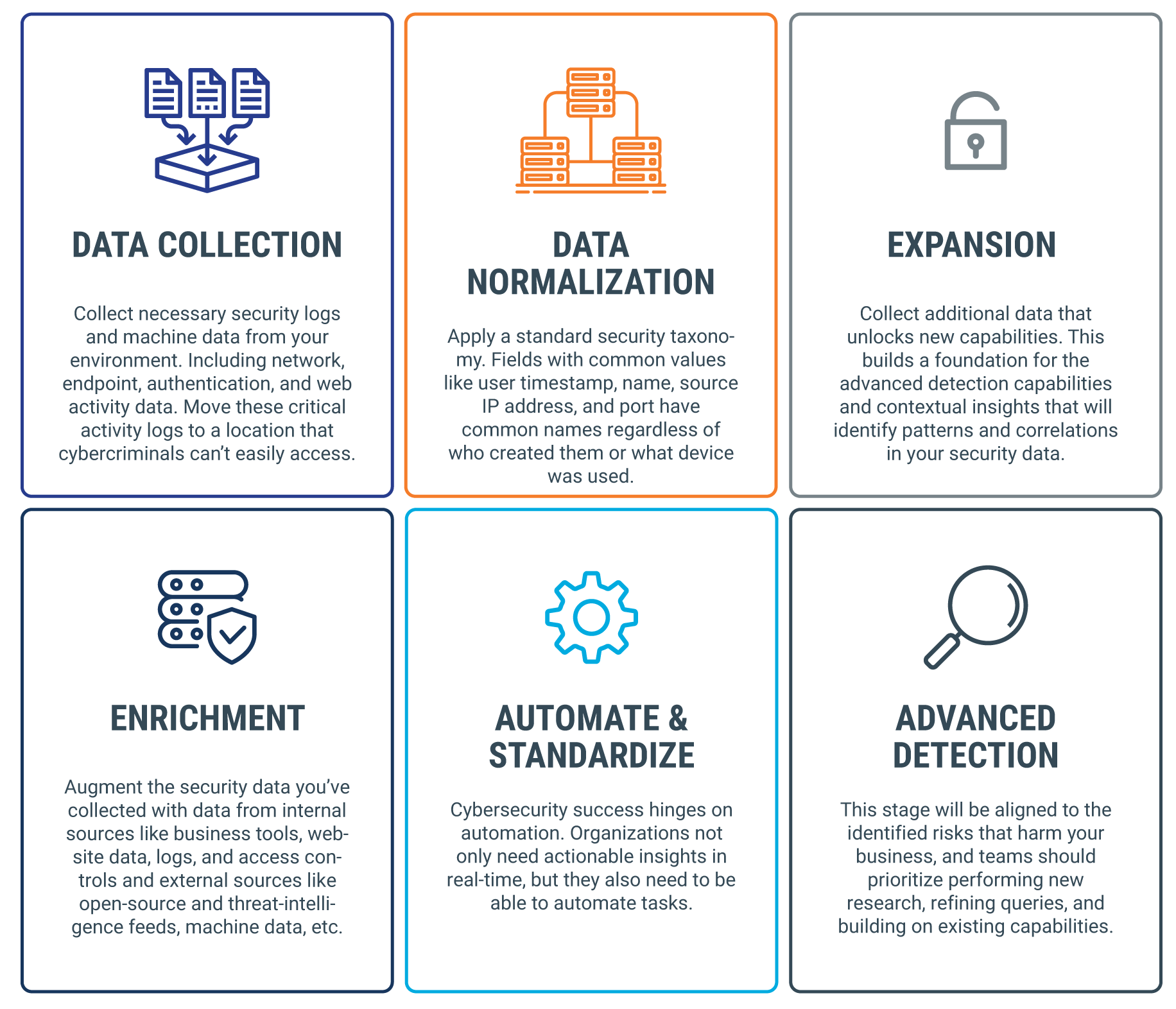
Data Analytics Cybersecurity Best Practices 3pillar Global

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero
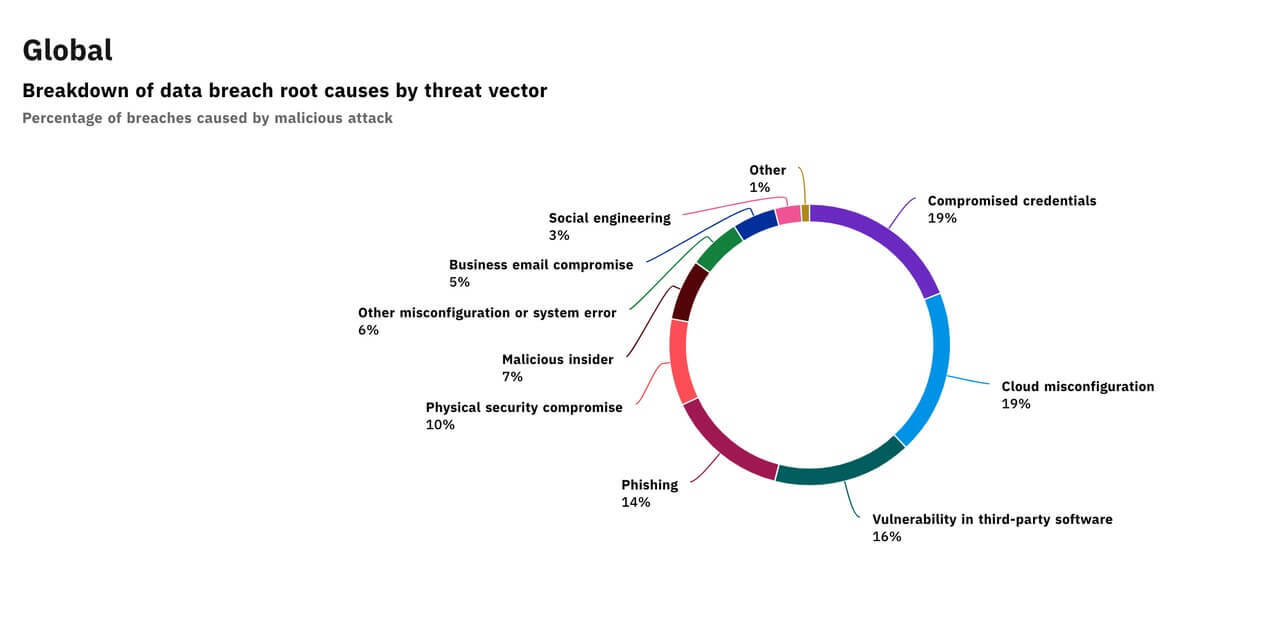
4 Security Measures Companies Implement After A Breach
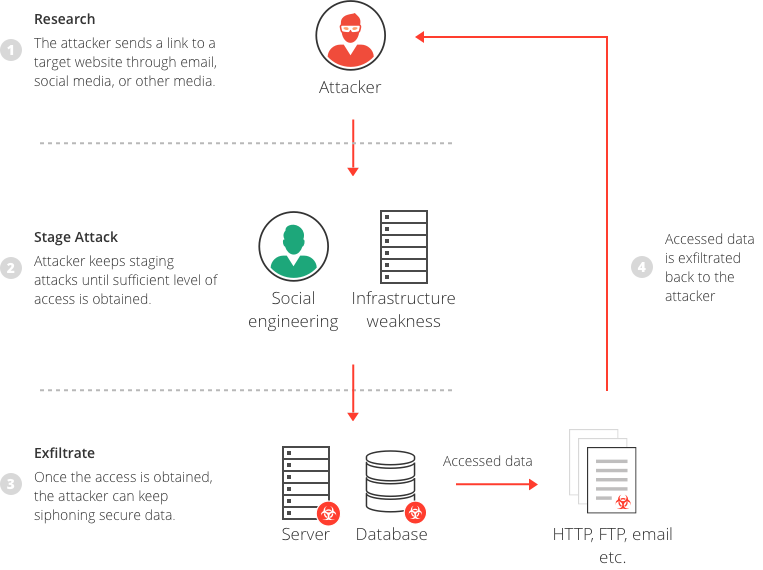
What Is A Data Breach Tips For Data Leak Prevention Imperva

Data Security Best Practices 10 Methods To Protect Your Data Ekran System

Solutions Cisco Breach Defense Design Guide Cisco

5 Critical Pieces Of A Good Security Playbook Axcient

20 Cloud Security Risks Cloud Cybersecurity Best Practices For 2022 Norton

Enterprise Data Breach Causes Challenges Prevention And Future Directions Cheng 2017 Wires Data Mining And Knowledge Discovery Wiley Online Library


